Please submit a business inquiry online.
-
Reporting and Deliverables
- September 20, 2016
- Posted by: Founder
- Category:
No Comments
Executive Summary
An appendix with supporting documentation and diagrams
Identification of discovered security vulnerabilities with severity rankings… -
Project Management
- September 20, 2016
- Posted by: Founder
- Category:

Own It Inc provide project management services in conjunction with their Information Security projects or they can work within your project management framework and provide your PM’s with assistance in initial scoping, detailed…
-
Network Assessment
- September 20, 2016
- Posted by: Founder
- Category:

Inventory of all WAN/LAN active network devices
Internet, VPN and overall perimeter review
Firewall and gateway structure -
Server Assessment
- September 20, 2016
- Posted by: Founder
- Category:

Document & Audit internal facing servers, providing software/hardware audits
Determine Patch/Vulnerability status of internal facing servers
Prioritization of servers based on risk -
Desktop Assessment
- September 20, 2016
- Posted by: Founder
- Category:
Document & Audit desktops, providing software/hardware audits
Determine Patch/Vulnerability status of desktops -
Facilities Assessment
- September 20, 2016
- Posted by: Founder
- Category:
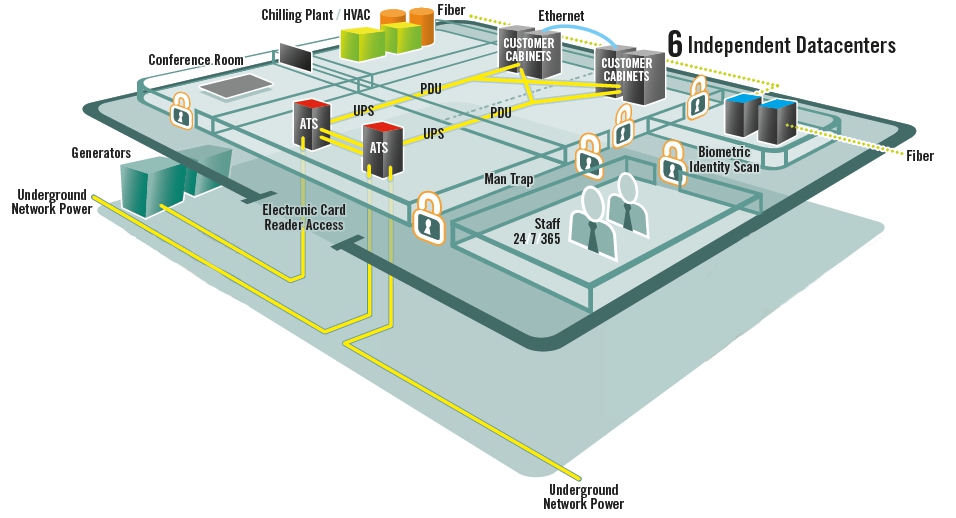
Power conditioning to include utilities, switch gear, UPS and generator
HVAC systems
Cable Plant (Physical Layer)
Heat, Smoke, Fire & Gas monitoring systems -
Documentation, Policies and Procedures Assessment
- September 20, 2016
- Posted by: Founder
- Category:

Physical security
Business Continuity/Disaster recovery
Policy Review
Test results review
Procedure review
Vendor Management -
Third Party Vendor Risk Management Assessment
- September 20, 2016
- Posted by: Founder
- Category:

Review of security policies and procedures
Human Resource Security
Risk and Asset Management
Incident Management -
Systems Hardening
- September 20, 2016
- Posted by: Founder
- Category:

Hardening of specific operating systems to reduce risk
-
Social Engineering Assessment
- September 20, 2016
- Posted by: Founder
- Category:

Building access
Telephone social engineering
Employee awareness interviews
Email phishing
- 1
- 2
Our clients depend upon the results we are privileged to produce for them. Wayne Miller has contributed directly to these results, helping us honor critical commitments.

